Activate account
Learn how to activate your FastPix account and authenticate with the API, obtain and manage access tokens, understand permissions, select workspaces, and handle admin-only access.
Activate your account
Before you can make API requests to FastPix, you need an active account and valid authentication credentials.
Sign up: If you don’t already have a FastPix account, create one here. Access level: Make sure your account has admin privileges only admins can create and manage API Access Tokens.
Once your account is ready, follow the steps below to generate your credentials.
Get your Access token ID and Secret Key
FastPix uses Access Tokens to authenticate API requests. These tokens serve as your API credentials, granting secure access to FastPix endpoints. All requests must include a valid Access Token and Secret Key via HTTP Basic Auth headers.
- Login to your FastPix dashboard
- Navigate to Settings > Access Tokens
- Click on Generate new token
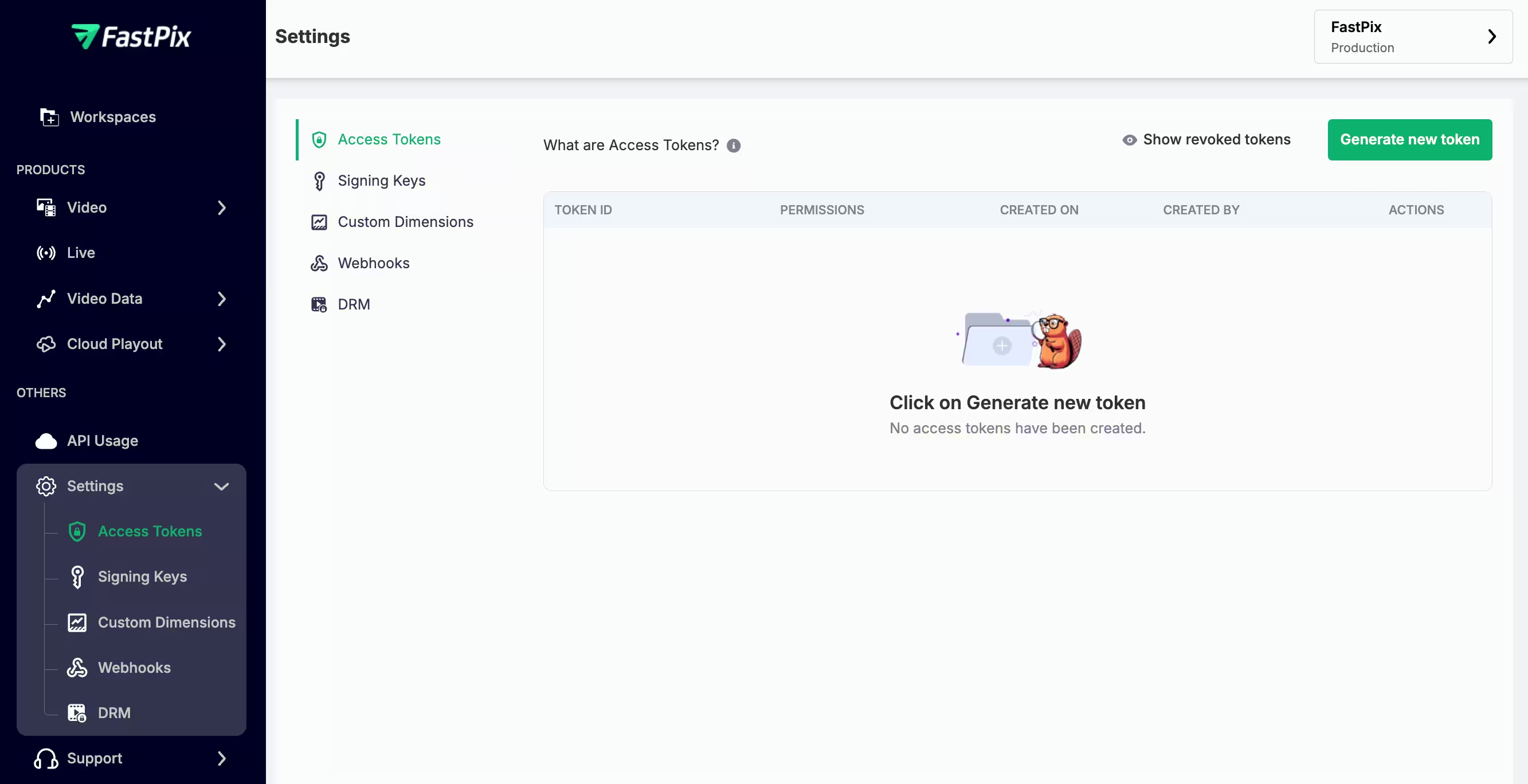
As a next step, a pop-up will appear with required inputs to create your new Access Token.
- Add your Access Token name
- Give permissions as per the purpose of using the Access Token.
- Next, click the Generate access token button
This action will generate your new Access Token ID and Secret Key.
PLEASE NOTE
For security reasons, FastPix only shows the Secret Key once. Download it immediately in a (.env) file or store it securely. If you lose the key, you’ll need to create a new token.
The Access Token ID and Secret Key you receive act like a key-pair, allowing you to access FastPix APIs that require basic authentication.
The Access Token ID serves as the username, while the Secret Key functions as the password.
How authentication works
FastPix uses HTTP Basic Auth to verify each API request.
To authenticate:
- Combine the Access Token ID and Secret Key as
username:password - Base64 encode the string
- Add it to the
Authorizationheader
Example header format:
Authorization: Basic base64(username:password)
Most HTTP clients and libraries will handle this for you.
Example request with cURL
Here’s an example of authenticating a request:
curl -X POST "https://api.fastpix.io/v1/on-demand" \
-u {Access Token ID}:{Secret Key} \
-H "Content-Type: application/json" \
-d '{
"inputs": [
{
"type": "video",
"url": "https://static.fastpix.io/fp-sample-video.mp4"
}
],
"accessPolicy": "public"
}'PLEASE NOTE
You can handle the base64 encoding of the username and password in your server-side code, allowing the library to manage the header details.
Access token permissions
Make sure your token has the right permission level:
- Read and write permissions: If you need to create and modify resources (e.g., media, direct uploads, live streams), ensure your Access Token has both read and write permissions.
- Read-only permission:
If your code primarily involves
GETrequests without creating resources, limit the Access Token to read-only permissions.
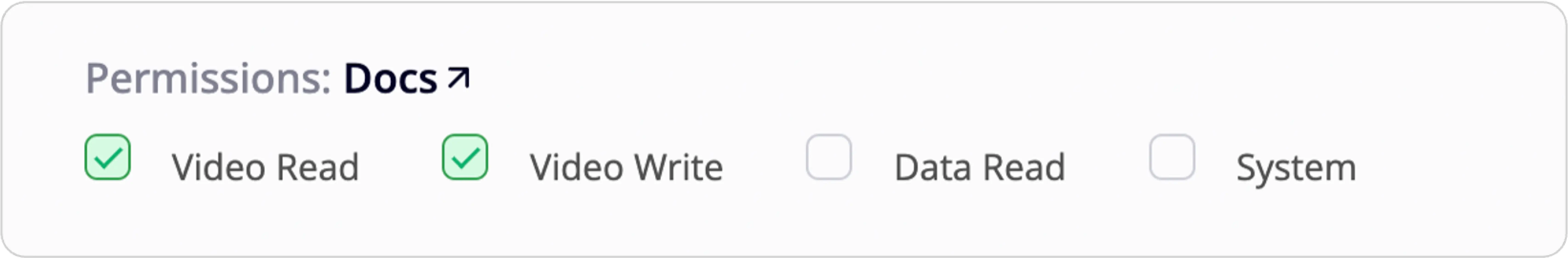
Revoke access token
In the unfortunate event of a leaked secret key (due to a security breach or accidental exposure), immediate action is necessary. Revoke the corresponding Access Token promptly. You can do this from the Org Settings page: Access Tokens. By revoking the token, you prevent unauthorized access and maintain the integrity of your FastPix account.
Admin and Member Access
FastPix supports two roles: Admin and Member. Both roles can view and manage all Access Tokens within the organization. They are responsible for:
- Generating new tokens
- Assigning and managing permission scopes
- Revoking expired or compromised tokens
Need some help? Contact Support
Something’s not right? Check System Status
Updated 4 months ago